Almost every investigation, whether it be a misdemeanor or a felony-level charge, has some type of electronic device involved. Frequently the most solid evidence is located on those devices making digital footprints imperative for tracking down suspects whereabouts, their activity and with whom they may be associated. Though digital information can be some of the most solid evidence in a case, the roadblock many departments face when it comes to downloading information is not obtaining the search warrant but actually extracting the information from the device once that warrant is signed.
State crime labs, though filled with expert knowledge, are severely overburdened with volumes of evidence. One phone can be time-consuming to comb through, let alone five from one case or 15 from multiple. The good news is there is no longer a need to wait for your state lab to process these devices; officers can now obtain the information and evidence they need on the spot.
Departments can now invest in software, training, and devices from sources such as Cellebrite, Susteen, and Oxygen Forensics. All are known for their software and physical products used to extract digital evidence. Recently, the advancement in technology for this way of gathering information has advanced through easier and faster tactics. Newer software works smarter not necessarily harder. By developing software that is user friendly, detectives, investigators, and officers on the street can gather the information they need easily and quickly. This not only helps speed up the investigation process but it allows officers to extract information from a device almost immediately allowing them to return the device to the owner.
“Digital intelligence can be overwhelming-criminal activity increases with data,” said Derek Brown, General Manager in North America for Cellebrite. “[Our] range of services for law enforcement is to help them as partners.” Brown says Cellebrite focuses on simplicity not complexity when it comes to their products and has created specific tools for each instance an officer may encounter.
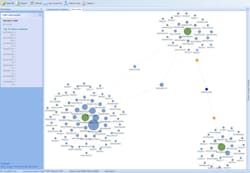
One of the best aspects of these devices is they are easy to use and easy to learn how to use. Oxygen Forensics Detective software is user friendly and is able to find passwords-encrypted or not. This particular software has image recognition capabilities as well. Not only does is the software compatible with phones, computers and other devices, bypasses passwords, but it is also able to extract data from drones by looking at the history of data and information stored. Oxygen Forensic Detective software can investigate through one interface providing one big overall picture of the data. It “maps” (displaying information of social activity) the data extracted from a device using analytical tools to uncover social connections, and other related data. It continues to provide details by building timelines, and sorting images, organizing it while protecting evidence as well.
The idea of social mapping allows investigators to delve into the activity of an individual’s phone or computer. Some forensic data software systems will be able to search a system based on a keyword or a name of an individual. The program will then sort through names and keywords and provide the investigator with a “map” and time stamps of when that person was contacted. There is no better way to have confirmed evidence than that with an actual time and date stamped on it. These maps are easy to read providing solid evidentiary value to the case.
If no evidence is found on a device, the device could theoretically be returned to the owner at that time. This can alleviate time expenses for things such as travel to and from the lab, and also alleviate burdens for evidence techs and evidence storage.”
— Retired Detective Jon Lund, formerly of the Ruidoso, NM, Police Department
Cloud Detective from Oxygen Forensics enables officers to download data from more than 80 applications including popular social media platforms. Imagine being able to acquire evidence on the spot, warrant in hand, without having to wait for a digital forensic analyst to extract the data for you. The ability to extract data from numerous cloud platforms provides officers with quick insight into a subject’s activity and may provide solid evidence needed for a case. It is also compatible with many platforms such as Android or Apple devices.
Susteen’s DataPilot 10 is a mobile device that allows officers and investigators to easily extract digital data. It’s about the size of your hand, is compatible with other forensic devices, and has five acquisition apps on it. Offering the ability to collect data on the spot can make a huge difference in your investigation as well as how your subjects, victims, and witnesses interact with you. The quicker you are to collect data and return their device to them, the more likely they are to cooperate with you as a whole, making your job a lot easier. The company’s Secure View enables investigators to gather, analyze, and formally report evidentiary findings quickly and easily.
“If no evidence is found on a device, the device could theoretically be returned to the owner at that time,” says Retired Detective Jon Lund, formerly of the Ruidoso, NM, Police Department. “This can alleviate time expenses for things such as travel to and from the lab, and also alleviate burdens for evidence techs and evidence storage.”
Within minutes officers can find out the information they need. He explains that devices like these systems cut turnaround time for cases, in that on-the-spot forensic examinations of devices can be performed instead of confiscating the items and sending them to labs for analysis.
UFED InField by Cellebrite offers officers the opportunity to collect digital evidence on the spot. Witnesses can now help officers without surrendering their phones for months on end. They can share a photo or text with an officer. (It is recommended that officers utilize this app only if they have a work phone—you don’t want your personal phone being subpoenaed for a court exhibit.) Data may also be extracted quickly by determining the type of device the information is being extracted from. Once that is specified, officers can acquire the information they require. Having that type of advantage can ease the mind of witnesses or involved parties in a case as well as enable the officer to gather information more quickly and conveniently. Brown says it allows data to be stored properly to help maintain the integrity of a case.
For a more permanent in-house set up, police departments have the option to set up a kiosk in their station for officers to extract data from phones with certain forensic devices as well. This way officers can extract the evidence they are looking for in a timely manner (at the office) and even return the phone to the owner quickly saving time, effort, and extra paperwork. It is much easier to retain the chain of custody when the officer is able to bring the device to their department, extract and save the evidence and then return it to the owner. Not only is this process convenient for all parties involved—it keeps the chain of custody tight.
Know what you’re doing
Of course, training is a necessity to be able to properly use these devices. And obtaining this type of training has become much easier. Cellebrite’s training academy has courses designed with departments and those who work in the field in mind. These courses range from beginner to more in-depth allowing the investigator to get as much training, basic or advanced, as they need. In particular, they offer Cellebrite Mobile Forensic Fundamentals, the Certified Physical Analyst course, and the Advanced Smartphone Analysis class. Lund says the Cellebrite training he attended was incredibly easy, and much of that had to do with how well the instructor taught the course, and since using the Cellebrite system is self-explanatory once the basics are understood.
Designed to suit departmental needs, Oxygen Forensics’ training options include online courses, webinars, and in-person instructor-led courses (one to five days long). Topics cover an array of areas from a beginner’s “boot camp” course, to extracting data from drones and more advanced analysis or extraction techniques. They have weekly webinars available on their site to keep investigators up to date on trends.
“These systems are worth the costs of the systems as well as the costs of the training,” says Lund.
There will always be exceptions when you have a device that is heavily encrypted and you will need an expert to take a look at it instead of depending on how encrypted a device is or the nature of the case itself. Though this is inevitable, having the right training and the proper equipment, can expedite your results. However, by having the right training and resources at your fingertips investigators can obtain faster results for their cases, expediting findings, and possible convictions.
Send it out for Help
By Jonathan Kozlowski
Should a captured device need digital forensics but be damaged beyond your in-house investigator’s abilities, there are services available for sheriff offices and correctional centers that can process the device and return results in days—not months. As part of the Securus’ Guarded Exchange program, law enforcement can send captured devices to a team of certified forensic staff utilizing state of the art forensic tools.
 Securus’ Guarded Exchange offers the cellular phone forensic chip-off. GEX certified forensic examiners perform data extraction of devices that are damaged, locked or unsupported by other forensic tools, using the latest chip-off forensics techniques. Chip-off forensics is the process of removing the flash memory from the printed circuit board of a device, using either a heat or no-heat method, depending on the purpose of the extraction, and reading as well as analyzing the raw data stored on the chip.Securus Technologies
Securus’ Guarded Exchange offers the cellular phone forensic chip-off. GEX certified forensic examiners perform data extraction of devices that are damaged, locked or unsupported by other forensic tools, using the latest chip-off forensics techniques. Chip-off forensics is the process of removing the flash memory from the printed circuit board of a device, using either a heat or no-heat method, depending on the purpose of the extraction, and reading as well as analyzing the raw data stored on the chip.Securus Technologies“Securus’ Guarded Exchange has provided integrated investigative solutions for the corrections industry since 2003, uniquely positioning the organization with proven expertise in monitoring, identifying and analyzing data, and turning that information into actionable intelligence for facility staff and investigators,” says Steve Schneider, Managing Director of Securus’ Guarded Exchange.
He explains that their analysts undergo extensive training to identify important pieces of information, such as images containing inappropriate content, mentions of facility staff by name, and other suspicious content that may raise warning signs for investigative attention—including interactions between an incarcerated individual to outside parties, social media posts, and even recognize if there is any allusion to communicating via USPs mail. In addition, Schneider adds that Securus associates conduct general investigative monitoring as well as accommodate specific requests from facility investigative staff working on cases.
Returned reports can be via CD, thumb drive or hard copy. However, Erik Thomas, Digital Forensic Lab Manager explains that facilities that adopt the Securus full suite of investigative tools have the benefit of integrated solutions, and would be able to import the forensic data into proprietary software such as THREADS, an intuitive program that cross-references data sets to help investigators recognize patterns and link connections.
More information can be found at Securustechnologies.tech/investigative/investigation/guarded-exchange.

Hilary Rodela
Hilary Rodela is currently a Surveillance Officer, a former Private Investigator, a former Crime Scene Investigator, and Evidence Technician. She worked for the Ruidoso (NM) Police Department as well as the Lubbock (TX) Police Department. She has written for several public safety publications and has extensive law enforcement and forensic training and is pursuing forensic expertise in various disciplines. Hilary is a freelance public safety writer and curriculum developer for the National Investigative Training Academy.