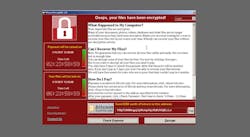
'Ooops, your files have been encrypted!' Should WannaCry be on Your Radar?
For reasons that escape me, some malicious software somehow got into the systems of various computers right around mid-May. I remember sitting here on this computer and seeing headlines flow in with this viral picture of a red pop-up screen covering up flight data in an airport terminal. As odd as it seems to think about what inspires people to cause such acts (see: "greed"), it was the type of reported victims that threw me. You see Hollywood's got it wrong. Hacking into the FBI in under a minute? No. Squirm your way into some bank system with "admin" or "12345" as the password? No. Apparently it's airports, factories, education, healthcare - to name a few - now. Again, I should not have been surprised at this list.
I'm just sad.
The software claimed to hold data for ransom - a time limit seems to tick down like a scene in "24". (I really wish there was a program named "Jack.Bauer.exe" to take it down now. That's a missed opportunity.)
If you hadn't been introduced into ransomware, I've connected this article to a few pieces we've published in the past. Links can be found to the side and/or at the end of this article.
WannaCry isn't 'New'
Steve Lasky, Editorial Director of SecurityInfoWatch.com and the magazines Security Technology Executive and Security Dealer & Integrator, reports a few figures in "WannaCry ransomware worm attacks the world":
- 2015 brought in almost 2,500 ransomware complaints accumulating to more than $1.6 million in payouts
- FBI estimates nearly $1 billion globally in payouts for 2016
- "they expect those numbers to double this year"
Lasky explains the infection exploited a vulnerability in the Windows OS. Anyone that had not installed the patch from March were at risk. He writes, "While cybersecurity experts admit that the spread of the infection has slowed today, they are worried that the new versions of the worm could be mutating and attack again at any time." (Is anyone else intrigued at the language of nefarious computer software programs? It's like we collectively picked biological labels and stuck with the theme.)
Gary Miliefsky, CEO of SnoopWall Inc., explained where WannaCry began, calling it the world's first ransomworm:
It all started when a group of hackers, called The Shadow Brokers leaked a bunch of NSA hacking tools onto the Internet. One of these tools is called EternalBlue, which, according to experts, is a perfect exploit for creating a Windows worm - software that attacks a Microsoft windows vulnerability and then installs on the next vulnerable windows system as it traverses the Internet. WannaCry is the first piece of ransomware ever to propagate using this kind of worm technology.
But, as mentioned before, WannaCry will certainly not be the last.
Putting this in perspective, Miliefsky offered a link to a rather intense online timeline: "World's Biggest Data Breaches" (at this writing it was updated as of April 25). In this tool you'll be able to click around the type of organization and method of leak. I found a bubble labeled "US Law Enforcement" between the 2010 to 2011 years linking to an article regarding a leak that year about the AntiSec hackers releasing 10 GB of personal information of public safety officers.
The big-ticket item that makes WannaCry different this time around has been the media. Aviram Jenik, CEO and co-founder of Beyond Security sees this as an opportunity, rather than mere talking heads blowing things out of proportion. "It's an opportunity to educate using current events. It is similar to how an earthquake in some other part of the world makes us all think about emergency preparedness."
Jenik answered my question if there were other ransomware strains PDs should be aware of: "There are countless, WannaCry was just the one that made the news. You can't be famous without a good name. Ask Marilyn Monroe, Elton John and Bruno Mars."
If you're interested in tracking malware/botnet around the world, check out the Malwareint (beta) at intel.malwaretech.com. The page describes itself, "Here you can view maps which display the geographical distribution of malware infection and time-series graphs of online and new bots (for fun there is a live map which will display a blip every time an infected computer pings one of my tracking servers)." The site is experimental and reportedly goes down from time to time. If it doesn't load for you, check back later.
How would a PD avoid ransomware?
I sought out sources to answer this question, I didn't have to look far. Michael Coppola of CJIS Solutions strongly encourages everyone – including law enforcement – to "stay up-to-date with operating system security patches and updates." He also reminds us to be wary of questionable emails.
Simply put, be wary if you feel it's odd, strange, or just an email link. Coppola even suggests double-checking your contact if they in-fact meant to send you something, "Now adays no one would be offended if you wrote them back and said, 'Hey John, can you confirm, you sent me this before I open it?'"
Miliefsky agrees with note of common sense worth repeating, "make sure you can trust the source before you [click links and download attachments]."
Other than being diligent with not opening questionable emails, again, Coppola puts it simple and straight forward: "Data backup is the ultimate protection of the files."
And, for him, offsite is key: "All technology can be hacked to some extent if there is a way to get to it. That is why off site data backup is the true method. No matter what happens to the original environment, you can always restore the good files."
He also brought up password security, reminding us all of the one thing I'm sure we're all guilty of - we should use complicated and different passwords. Passwords unique to each website and opting for two-factor authentication if the option is offered.
Review your agency's email policy. Maybe even remind officers of good and safe email practices. And plan on handling the vulnerability left from not updating Windows. "If you have not yet been exploited, move quickly to close the hole," says Miliefsky. "If you have not installed Windows Security Update MS17-010, please take the time to install the proper patch for your version of Windows and do it quickly: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx."
"Any netowrk administrator who has followed a proper patching routing and has done a security scan in recent months would have found and fixed the security hole WannaCry used," says Beyond Security's Jenik. Ensure patches are installed and run a monthly scan to makes sure they were installed correctly.
Miliefsky also suggests making sure your handheld devices are up-to-date as well, suggesting to contact the manufacturers and demand "security by design." He provided a couple of links to third-party articles regarding network security and the Windows firewall:
- Harden your network - https://chrisreinking.com/stop-cryptolocker-from-hitting-windows-file-shares-with-fsrm/
- Close inbound traffic - http://www.computerworld.com/article/3197421/networking/the-windows-firewall-is-the-overlooked-defense-against-wannacry-and-adylkuzz.html
Are law enforcement agencies still at risk? Are police department computer systems a potential victim of ransomware? Truth is yes. In all honesty, they never won't be. Correcting common vulnerabilities – and that includes human behavior - can be the one of the biggest steps you can take in keeping data secure.
Related articles to check out about network security and cybercrime:
- The Ransomware Threat
- ALERT: Ransomware and Crypto Virus
- "Advanced Authentication" Deciphered in the Computer Wizarding World
- Back to the Academy for Cybercrime Training
- From Streets to the Servers, the Newest Crime Wave is Here
- The Enemy is at the Gates! Ignore Cybersecurity at Your own Risk
- Securing Cyber Space
- Ransomware is also featured on the cover of the June 2017 issue of Security Dealer & Integrator.

Jonathan Kozlowski
Jonathan Kozlowski was with Officer.com, Law Enforcement Technology, and Law Enforcement Product News from August 2006 to 2020.
As former Managing Editor for Officer Media Group, he brought a dedicated focus to the production of the print publications and management of the Officer.com online product and company directory. You can connect with Jonathan through LinkedIn.
Jonathan participated as a judge for the 2019 and 2020 FOLIO: Eddie & Ozzie Awards. In 2012, he received an APEX Award of Excellence in the Technology & Science Writing category for his article on unmanned aerial vehicles (UAVs) in police work, aptly titled "No Runway Needed".